Perhaps it was an unexpected gathering on your high school footy oval, breaking the tedium of a math lesson. Or it could have disrupted a bustling Monday morning in the office. Each of us has experienced the inconvenient — but essential — ritual of a fire drill.
Regardless of the disruption they cause, everyone understands the importance of the exercise. Fire drills are like going for medical check-ups, servicing the car, and backing up hard drives — things that seem tiresome now, but which we wish we’d done when disaster strikes. They exemplify how precautionary measures today can mitigate risks tomorrow.
While most businesses have plans in place for fires and medical emergencies in the workplace, very few Australian businesses are actively preparing for a cybersecurity breach.
Cybercrime is on the rise as recorded by the Australian Cybersecurity Centre, and accordingly to ACSCs Annual Cyber Threat Report from 2021 to 2022, one cybercrime report is made every 7 minutes, and this frequency is rising (See Figure 1).1
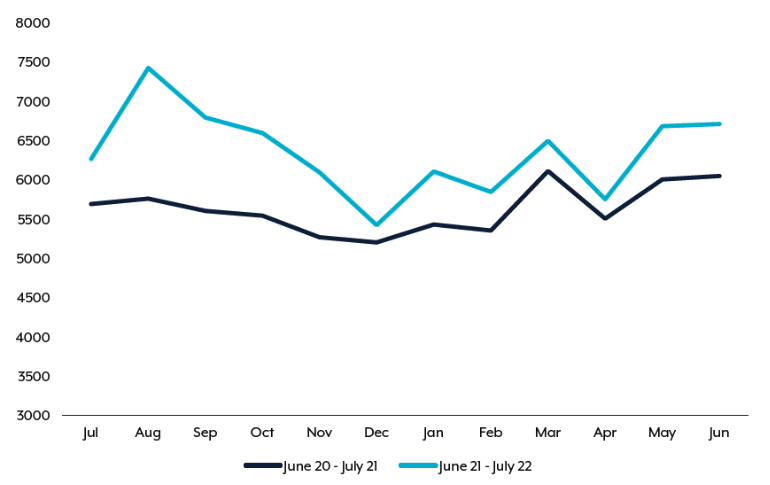
Figure 1: Cybercrime reports by month for 2021-2022 financial year compared to the 2020-2021 financial year.1
In today's digital landscape, where cyberattacks and data breaches have become alarmingly common, organisations must prioritise cyber crisis management. Cyberattacks can lead to emergency situations, with confidential information hacked, customer trust shattered, and financial losses mounting. Effective leadership is crucial in these scenarios. Cyber crisis management involves proactive planning, rapid response teams, and robust protocols to mitigate, manage, and recover from cyber incidents swiftly. With the growing frequency and sophistication of cyberattacks, businesses must be prepared to navigate these crises with finesse. Let's delve into the world of cyber crisis management and explore how it can safeguard your organisation against potential catastrophe.
The impact of cybersecurity threats, breaches and attacks
A cybersecurity breach is a catastrophic event with wide-reaching effects. In the immediate aftermath, it can expose customers' private data and impose substantial crisis-management costs on businesses. Over the long term, it can inflict irreversible harm on a company’s reputation.
From legal consequences due to non-compliance with data protection regulations to operational disruption such as productivity losses due to system paralysis from a ransomware attack, cyber threats cause many issues to a organisation's function, finances and brand.
The potential severity of such an incident makes proactive cybersecurity crisis management an essential exercise for any business that stores important data. This is especially the case in industries that are more susceptible to a cybersecurity breach due to the sensitive nature of the data and information they tend to store — including financial services.
The importance of cyber crisis management in an organisation and associated risks of not preparing a response plan
Crisis management strategies in response to cyber breaches are often reactive rather than proactive. While reactive strategies require less work upfront, they represent a pitfall that has been devastating for many businesses’ reputations.
This was the case when Optus disclosed its significant data breach — affecting almost 10 million users — in September 2022, which led to a 25% spike in negative media coverage of the company. Overall positive sentiment about Optus plummeted from its usual rate of 18% down to just 5%.
The company looked ill-prepared and irresponsible. Adding to this problem was the fact that companies like Optus — where customers maintain an ongoing (and ideally trusting) relationship through memberships or subscriptions — are particularly vulnerable to the fallout of data breaches. Generally, the most significant breaches correlate with a 5–9% reduction in reputational intangible capital.
If Optus had a comprehensive cybersecurity crisis response plan in place, it would likely have weathered the storm better than it did. But what does such a plan look like?
What effective cyber crisis management entails
Preparation for a cyber-attack (or any kind of cyber crisis) involves not only thinking about the post-attack response but also not only addressing the post-attack response but also the planning, assessment, and testing phases of a cybersecurity breach.
As depicted in Figure 2, to build effective cybersecurity operational resilience after a breach, you need to bridge the gap between crisis management, crisis communication, and cybersecurity — a connection often neglected in cyber safety protocols.
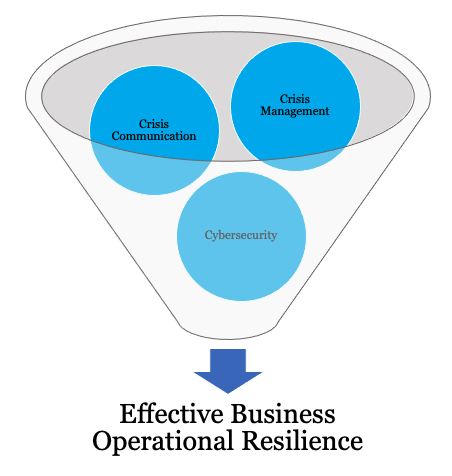
Figure 2: Creating effective cybersecurity operational resilience
At BlueChip, we guide our clients through the following stages of becoming cyber-crisis ready.
Prevent
Being proactive is key in cyber crisis management. The prevention stage includes the identification of the cybersecurity threats the organisation might face, and doing a careful assessment of the risks and potential impact of a breach. We ask, what can be done now to mitigate these risks for your business? The prevention stage also involves assessing whether the organisation has adequate training for all employees on how to conduct themselves during and after the event of a cyber breach.
Prepare
The preparation phase, the most comprehensive of the three, involves implementing systems and protocols to support the business in the event of a cyber breach. This includes formulating plans, allocating resources, establishing relationships with cybersecurity experts, and securing cybersecurity insurance that accounts for potential PR and communication damages. Implementing robust threat detection systems and continuous monitoring tools can further help organisations stay one step ahead of cyber threats.
Practice
This stage includes testing the organisation’s cybersecurity management capabilities against a simulated crisis scenario. Simulations like these provide crucial insights for further refining the crisis management plan.
The work in these three stages combines to unlock your business’s capacity to predict and preempt potential future cyber risks, and plan comprehensively for their management. Such a plan maximises a business’s chances of maintaining trust with its customers and remaining afloat in the event of a breach.
Running a cybersecurity crisis simulation is an important exercise where your business can implement and test a cyber crisis response plan in a breach-like scenario. Here at BlueChip, our founder Carden Calder, alongside the team at Horizon GR, have developed and launched a simulation practice specific to Australian Businesses, to learn more about how it works and get your team prepared click here.
Creating a Cyber Crisis Management Team
As part of our 'preparation' phase, we recommend establishing a dedicated team trained to respond to a crisis scenario. This team should include:
- A cybersecurity crisis management leader to steer the entire incident response and coordinate the team's efforts to ensure effective management
- A crisis management team who monitor and evaluate risks, manage resources and are trained in the organisation's cybersecurity strategies
- A crisis communication team and manager- the manager should keep stakeholders informed about the incident, its impact, and the response measures, while the wider communication team develops appropriate messaging strategies to mitigate reputational damage
- IT specialists well-versed in cyber crisis prevention and response techniques who can manage the technical aspects of a cybersecurity breach
These teams should coordinate not just during a crisis, but regularly, to enhance response strategies and soften the impact of a cybersecurity breach.
Cyber Resilience
Effective cybersecurity protocols and risk management plans are never 'one-size-fits-all' models. Experts agree that adopting an umbrella approach not only produces an inadequate strategy for future crises, but it also sets unreasonable expectations for the nature of organisational crises themselves. Cyber breach incidents are dynamic and rapidly adapt to technology changes. Therefore, risk management plans must reflect this adaptability to respond to the specifics of a given problem.
To help you get a head start in preparing your own cyber crisis management and become more resilient in the face of cyber-attacks, we have created a self-assessment tool consisting of only 14 questions which will help in guiding you to locate specific vulnerabilities your organisation has in relation to cybersecurity crisis management, to download your own copy, click here.
The time to think about a crisis isn't during the crisis itself. It's imperative to treat the threat of a cybersecurity breach with as much seriousness as we do a fire. To ensure the success of cyber crisis management initiatives, it is essential for organisations to adopt a proactive approach rather than a reactive one.
In today's digital age, the risk of data theft and subsequent reputational damage is too high to ignore. By prioritising cybersecurity and investing in comprehensive strategies, businesses can reduce the likelihood of breaches occurring and minimise their impact when they do happen.It's time for comprehensive risk management strategies to be implemented across all organisations.
References consulted
1 Australian Cybersecurity Centre, ‘ACSC Annual Cyber Threat Report, July 2021 to June 2022’ (Australian Cybersecurity Centre2022)
Biddle N, Gray M and McEachern S, ‘Public Exposure and Responses to Data Breaches in Australia: October 2022’ (2022)
Elsworthy E, ‘“An Ad Is Not a Strategy”: Federal Government Fury at Optus’s Apology in Weekend Newspaper’ (SmartCompany3 October 2022)
Lowe S, ‘What Is as 3745:2010 All About?’ (Workplace Emergency Management3 October 2019) accessed 4 July 2023
Stone K, Zogby M and Garcia C, ‘Lessons from a Year in Crisis: Do’s and Don’ts of Crisis Management’ (Defense Counsel Journal 2022)